Setting Up CIS Benchmark 2.4.5 In macOS
Ran into a tricky one when attempting to implement CIS Benchmark 2.4.5 on the machines in my company’s fleet.
For starters, my co-worker and I discovered two different 2.4.5’s.
One is from CIS’s official Monterey 1.0.0 PDF document, and is titled:
Ensure Remote Login Is Disabled.
The second is from the macOS Security Compliance Project
, and is titled:
Disable SSH Server for Remote Access Sessions.
Just to cover our bases, we decided to combine the two given commands into one script.
Ensure Remote Login Is Disabled’s command is the following:
systemsetup -setremotelogin off
Disable SSH Server for Remote Access Sessions' command is as follows:
/bin/launchctl disable system/com.openssh.sshd
Generally we would just combine the two, and get a script like this:
|
|
All done, call it a day, right? Of course not. Why would it be that easy?
The issue here is that systemsetup -setremotelogin off
asks a question:
Do you really want to turn remote login off?
If you do, you will lose this connection and
can only turn it back on locally at the server (yes/no)?
So we will need to add a yes command, then pipe that into
the systemsetup command.
We will then get the following script:
|
|
Now when we run the script:
setremotelogin: Turning Remote Login on or off requires
Full Disk Access privileges.
Another error!
The script is working, but the lack of access is preventing it from doing its thing.
The obvious option in this case would be to go into System Preferences > Security & Privacy, and grant the Terminal Full Disk Access.
However, we don’t want to do that manually for the entire fleet, so we will use our trusty MDM to handle this for us. In this case, Jamf.
You’ll want to create a Configuration Profile as follows:
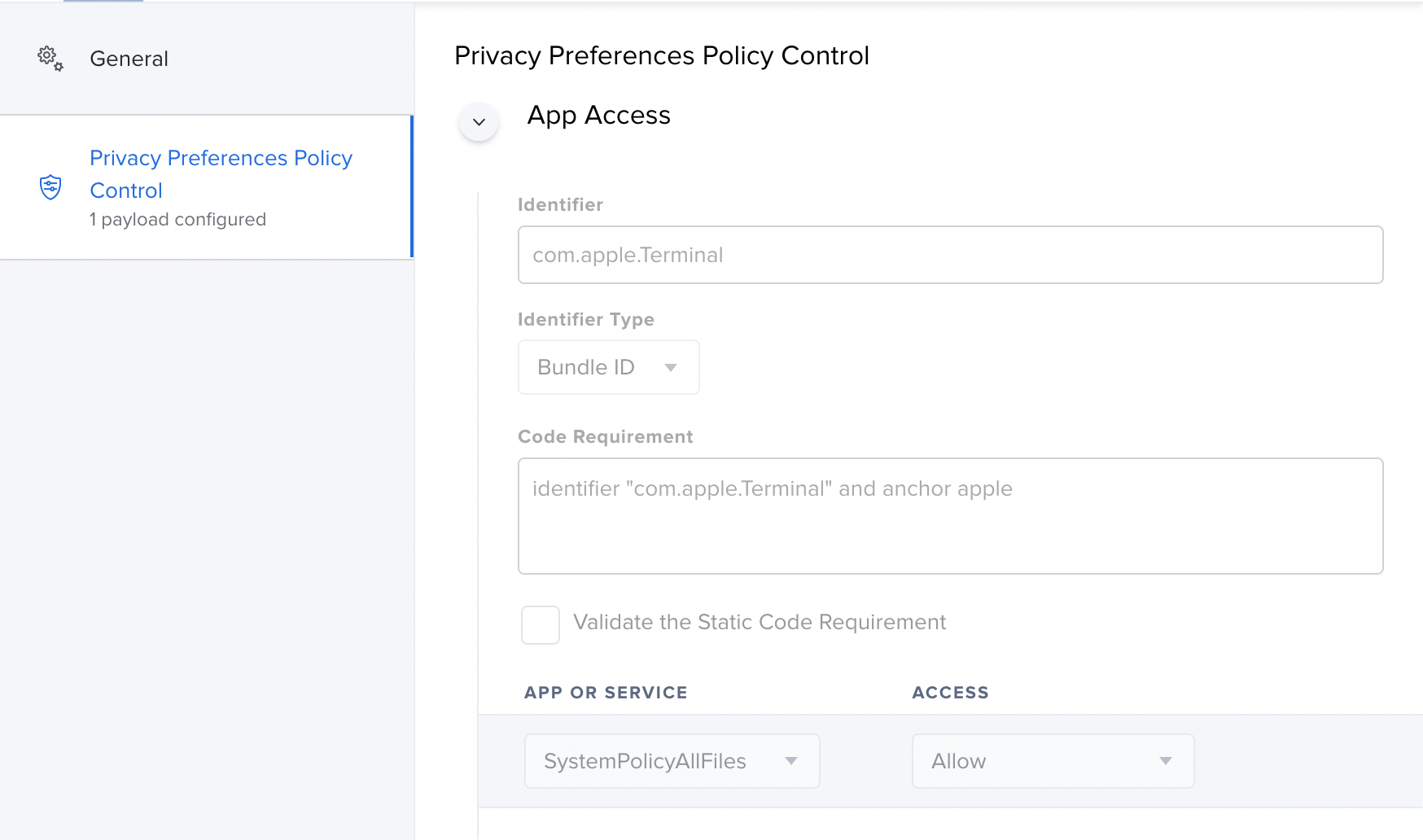 This will now allow items that are run via Terminal commands to access the full disk.
This will now allow items that are run via Terminal commands to access the full disk.
You can also create Privacy Preferences Policy Controls via the
Jamf PPPC Utility.
Once the Configuration Profile is set, you can run the script with no issue.
Finally, as a check you can use the systemsetup -getremotelogin command:
systemsetup -getremotelogin
Remote Login: Off
Take it easy y’all.